Application Whitelising: Securing Data Encryption Through Controlled Execution
While data encryption forms a fundamental layer of protection, ensuring only trusted applications can access and process encrypted data is equally...
3 min read
 DriveLock
Feb 2, 2024 2:45:45 PM
DriveLock
Feb 2, 2024 2:45:45 PM

The number of attacks is constantly increasing and attackers are becoming more and more targeted and tricky. They specifically exploit the human factor by wrapping phishing emails as deceptively genuine. USB sticks and removable storage devices are still one of the most common sources of malware infections. In "traditional" attacks, external malware is primarily installed or executed on the target system. In addition, in "living off the land" (LotL) methods, also known as "fileless malware", attackers use administrative or system tools that are already in place on the target system to initiate an attack, i.e. scripts or software macros such as PowerShell or MS Office.
| TABLE OF CONTENT |
In today's rapidly evolving digital landscape, new cybersecurity threats pose significant challenges to both individuals and organizations. The increase in sophisticated ransomware attacks, where cybercriminals encrypt sensitive data and demand a high ransom for its release, continues to rise, targeting businesses, healthcare facilities, and even critical infrastructures. Even when companies are willing to pay the demanded ransom to decrypt their data, they may still need to make an additional payment to prevent the disclosure of sensitive information. This is quite insidious.
According to a study by the German BSI, there are 117 million new types of malicious software each year - more than 320,000 per day.
The problem with antivirus software based on pattern recognition is that it only detects known malware. However, malware can disguise itself or may not be known at the time of an attack. Zero-day exploits and living off the land (LotL) attacks can be the consequence.
The belief that you are safe from such threats with an antivirus solution is unfortunately mistaken. Considering the "revenue" volume involved per month, one can imagine that there isn't just a petty criminal on the other end. Instead, we are dealing with a professional industry.
Relying solely on conventional security measures leaves vulnerabilities open, making it essential for businesses to implement a comprehensive strategy that addresses various attack vectors and ensures robust defense against evolving threats. Application Control rises to these new challenges and proves to be an effective protection against new and rapidly changing threats.
Application Control allows administrators to manage the execution of any application on computers. According to the company's strategy, different rules can be applied that determine which applications are allowed to run and which are blocked.
Application Control plays a crucial role in your security strategy. It allows you to approve only the software, software libraries, and scripts needed for productive work. On the other hand, you can block built-in tools that attackers could misuse or restrict their use to certain administrative groups. The configuration for Application Control is centrally managed within DriveLock policies and can be targeted to all computers or limited to specific groups of people. You always retain control. DriveLock's "predictive" allow-listing minimizes the maintenance and ensures security standards through the automated learning of lists by preventing the installation and execution of unknown applications. This approach prevents cyber attacks from any type of file-based and file-less malware, including ransomware and Advanced Persistent Threats (APT).
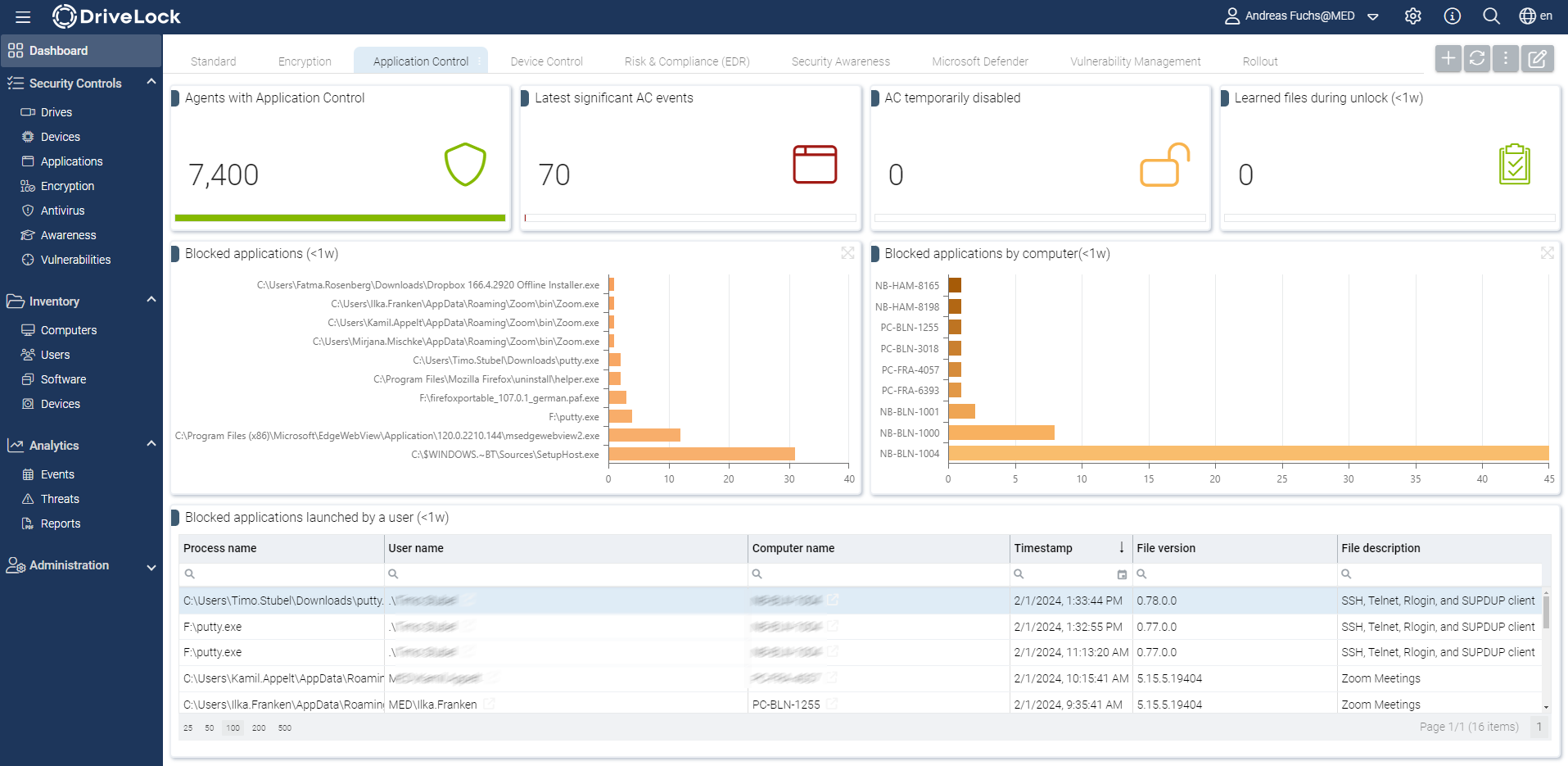
Before you start blocking programs, simulation modes are available to test the effects of your rules in advance. During a simulation, DriveLock generates event messages for applications that are started or blocked according to the rules, but the execution itself is not yet prevented. The simulation mode can be very useful to determine which applications would have been blocked. Subsequently, you can analyze the data with the help of the DriveLock Operations Center in an easy manner to quickly find relevant events. This mode is ideal for a step-by-step introduction into production environments.
The approach of using static block- or allow-lists for applications is only partially effective in rapidly changing situations, and administrators often complain about the disproportionate maintenance effort required. The intelligent allow-listing offered by DriveLock minimizes maintenance efforts through automated learning of lists.
Existing software distribution and patch management systems can be easily designated as so-called Trusted Installers. As a result, managed applications are automatically allowed.
Based on DriveLock Application Control, Application Behavior Control provides additional security for companies by "teaching" your applications to behave correctly.
For example, you can specify that no other application (or process, script) that could pose a potential risk to the system is started from an authorized application. Or you can define what kind of access a particular application is allowed (e.g. read or write access to files or the registry).
Application Control prevents users from installing, executing unauthorized applications, or opening attachments. Thus, companies also get a handle on Shadow IT.
A central console provides comprehensive administrative dashboards and allows administrators to gain insight into the corporate environment. This includes endpoints activated with Application Control, the status of their respective learning behaviors, and events for blocked and allowed applications.
DriveLock offers effective support for companies to protect themselves against cyberattacks, prevents data loss, and complies with regulatory requirements.
With Application Control, DriveLock provides effective and preventive protection against known and unknown malware. Our solutions reliably protect people, companies, and services from cyberattacks and the loss of valuable data.
Read more in our whitepaper: DriveLock Application Control
With the DriveLock HYPERSECURE Platform, cyberattacks stay where they belong: outside!

While data encryption forms a fundamental layer of protection, ensuring only trusted applications can access and process encrypted data is equally...

In today's rapidly evolving digital landscape, endpoint security stands as the frontline defense against a myriad of cyber threats. As organizations...

In today's digital world, cyberattacks are a constant threat, and adware attacks are one of the most common forms of malware. Adware can not only...