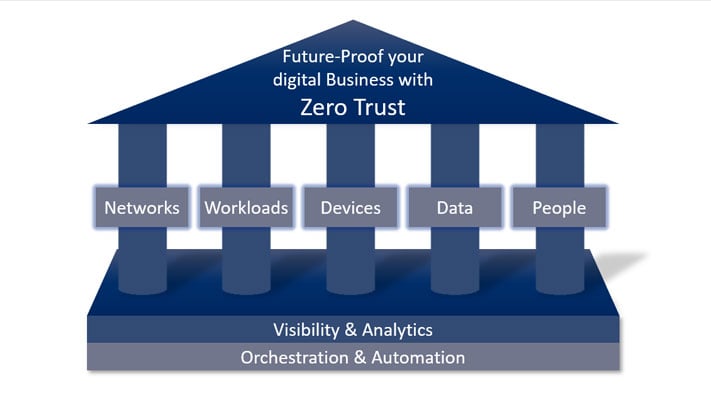
7 principal pillars of Zero Trust Model
The major strategic goal of cyber security in the digital age is to combat and mitigate data breaches. A company's data is its most valuable asset to...

↑ Listen to the blog article
Risk lies around every corner and should be expected at any time. In the world of IT, risk is inherently everywhere and comes in many shapes and forms. Consequently, the task of writing down all possible risks threatening an IT infrastructure can be daunting and never-ending.
Endpoint Security Concerns: Endpoints are vulnerable due to data volume, application variety, internet access, potential for loss/theft, device connectivity, BYOD policies, and user susceptibility to phishing.
SPE Model: Assess risks using the Severity, Probability, and Exposure (SPE) model, where Risk = Severity x Probability x Exposure.
Practical Use: The SPE model helps quantify risks and can be applied using tools like the DriveLock calculator for tailored risk assessment.
| TABLE OF CONTENT |
However, brainstorming all possibilities of threats looming around IT systems is an absolutely necessary job to know what, when, where and how to defend.
A risk assessment is a fundamental process for any organization seeking to protect its assets. It involves a structured approach to identify potential dangers, analyze their likelihood and impact, and determine appropriate responses.
In cybersecurity, a risk assessment specifically focuses on the threats and vulnerabilities that could compromise an organization's information systems, data, and digital assets. This process is crucial for understanding the organization's security posture and making informed decisions about resource allocation for risk mitigation. Key tasks within a cybersecurity risk assessment include:
Asset Identification: Cataloging all valuable digital assets, including hardware, software, data, and network infrastructure.
Threat Identification: Recognizing potential threats that could exploit vulnerabilities, such as malware, phishing attacks, insider threats, and natural disasters.
Vulnerability Assessment: Identifying weaknesses in systems, applications, or processes that could be exploited by identified threats.
Likelihood and Impact Analysis: Evaluating the probability of each threat occurring and the potential consequences to the organization if it materializes.
A thorough cybersecurity risk assessment follows a systematic series of steps to ensure comprehensive threat identification and effective mitigation strategies. Understanding these stages is crucial for any organization aiming to safeguard its digital assets. The following outlines the seven key steps involved in conducting a robust cybersecurity risk assessment.
Risk Identification: This step involves identifying all potential security threats and vulnerabilities that could affect the organization's information systems. This can include external threats like hackers, malware, and phishing attacks, as well as internal risks like unauthorized access by employees or system failures.
Risk Assessment: In this phase, the identified risks are assessed based on two main factors: the likelihood of the risk occurring and the potential impact it could have. The assessment can be qualitative (low, medium, high) or quantitative (assigning numerical values to likelihood and impact) based on the organization's preferences and available data.
Risk Evaluation: After assessing the risks, they are evaluated to determine which ones pose the most significant threat to the organization. This involves considering both the likelihood of the risk occurring and the potential impact it could have on the organization's operations, data integrity, reputation, and more.
Risk Mitigation: Once risks are identified and evaluated, organizations develop strategies to mitigate or reduce those risks. Mitigation strategies can include implementing security controls, using encryption, conducting regular security training for employees, and adopting best practices for network and system management.
Risk Acceptance: Some risks might be deemed acceptable, especially if the cost of mitigation outweighs the potential impact of the risk. In such cases, organizations might choose to accept the risk but put in place contingency plans to respond effectively if the risk is realized.
Risk Communication: It's important to communicate the results of the risk assessment to relevant stakeholders within the organization. This ensures that everyone is aware of the potential risks and the strategies in place to address them.
Ongoing Monitoring and Review: Risk assessment is not a one-time event; it's an ongoing process. Organizations need to continuously monitor their systems for new vulnerabilities and threats, reassess risks periodically, and update their risk mitigation strategies as needed.
From an endpoint secutiry perspective, risk assessment models as well as information security regulations take it very seriously. At the endpoint, there are massive potentials for attack, and this is because of:
Many models have been developed for risk assessment. An easy yet effective one is the Severity, Probability and Exposure (SPE) model. The SPE model offers a straightforward yet powerful framework for conducting a risk assessment. This model evaluates risk by considering three key dimensions. It works as follows.
Risk = Severity x Probability x Exposure
Severity: Severity is an event’s potential consequences measured in terms of degree of damage, injury, or impact on a mission. Severity can vary from 1 to 5.
Probability: Probability is the likelihood that the potential consequences will occur. Probability can vary from 1 to 5.
Exposure: Exposure is the amount of time, number of occurrences, number of people, and/or amount of equipment involved in an event, expressed in time, proximity, volume, or repetition. Exposure can vary from 1 to 4.
By analyzing these three factors together, the SPE model provides a valuable method for prioritizing cybersecurity risks and informing mitigation strategies.
Curious? You want to assess your own risk?
We have provided you with a tool. Click here for your individual SPE Calculator:
(Excel file)
Need help putting your SPE Score into context and identify sensible measures to reduce risks in certain areas? Our Consulting Team is here for you.
The major strategic goal of cyber security in the digital age is to combat and mitigate data breaches. A company's data is its most valuable asset to...

User management is a cornerstone of robust cybersecurity strategies. Whether you are an experienced IT professional in a critical sector such as...

In our increasingly interconnected world, where data flows freely and digital landscapes expand at a breakneck pace, the need for robust...